Stealth Piracy App Evaded Apple Again? Just the Tip of the Evasion Iceberg
 The positions of Apple and Google are very clear when it comes to piracy app availability in their respective stores. Whether created for iOS or Android, they are not allowed. Period.
The positions of Apple and Google are very clear when it comes to piracy app availability in their respective stores. Whether created for iOS or Android, they are not allowed. Period.
With the theory neatly wrapped up, reality tends to take over and at that point, the bright lines become a little blurred. Right now there are apps on the App Store and Google Play which offer TV schedule/EPG-type functionality out of the box, exactly as advertised. However, a tap here and an adjustment there reveals new functionality mentioned nowhere in official product descriptions.
Stealth Piracy
A report late last week revealed that an iOS app called “Collect Cards: Store Box” which claimed to manage photos and videos, had hidden its true potential away for more than a year.
This wolf in sheep’s clothing was reportedly a full-blown pirate streaming app offering content from Netflix, Disney+, Amazon Prime, HBO Max, even Apple TV+ according to the report. Such was the app’s success, it made it the top #2 slot on the App Store in Brazil; through the use of geo-blocking, users of the app in the United States weren’t shown the illegal features, which limited the chances of being quickly shut down.
Tactics like these aren’t new. Piracy functionality has been hidden inside puzzle games and Shazam-like audio recognition apps, on both the App Store and Google Play. The music industry has complained that apps that don’t make any real effort to hide have also been able to evade vetting.
Apps and App Stores Discussion Paper
These issues and more are addressed in a new discussion paper released this month. Titled Apps and App Stores, the paper is based on the work of the EU’s Intellectual Property Office Observatory’s Expert Group on Cooperation with Intermediaries. The paper doesn’t represent the official position of the EUIPO but does provide an interesting overview of piracy-related problems in connection with mobile apps.
Mainstream app stores have systems in place to screen apps and their updates. In part this is to prevent infringing apps from being offered to the public, but developers can employ various evasion techniques to undermine that.
Evasion Techniques
As well as disguising piracy apps as something more benign, malicious code and/or infringing functionality can be hidden from the review process using encryption or delays. Additional code can be installed after the initial review, or following a subsequent update.
The paper also touches on apps behaving differently depending on the region and by changing when an app is made available. The report says that developers have been observed “hiding the app from their account and subsequently on the app store during certain days of the week to avoid detection from right holders.”
Rather than using encryption or other techniques that provide an element of stealth, other apps are said to operate right out in the open by simply claiming to be a legitimate service.
“[S]ome apps, purportedly disguised in a false appearance of legality, dissociate themselves from the illegal sharing of protected content they support, which is the core of their activities. These apps have terms and conditions highlighting their neutral nature with regard to the content used through their services, which do not reflect on the reality of the service provided,” the paper explains.
“This may lead app stores to require additional information and proof of the illegal nature of the app from right holders before making a decision on whether to block or remove the app in question.”
Third-Party App Stores
From the perspective of the average user, iPhone and iPad devices running iOS are restricted to content available from their respective app stores. For Android users, however, the app landscape is much more open. It’s likely that most users will be satisfied with Google Play, but on Android it’s trivial to allow apps not obtained from the official store to be installed on a device.
As the ‘stealth’ app issue demonstrates only too well, app store review processes are not bulletproof. However, users who ‘sideload’ apps using alternative app stores, or even randomly from anywhere else on the internet, expose themselves to apps (APK) that in many cases undergo no review whatsoever. While that doesn’t automatically make these apps unsafe, there’s nothing in place to ensure the opposite either.
The discussion paper notes that software is available from official app stores that may be able to identify potentially malicious apps and alert users to prevent installation. The paper also cites an article published by TF in 2023 in which we offered some basic tips on how to use beginner-friendly tools to reduce exposure to malicious Android software.
Don’t Install Any Mobile App Before Testing It
When users are 100% confident that the source of the app they wish to sideload is safe, there is almost nothing anyone can do to convince them otherwise. Other users may be more on the fence; while they may generally trust the source, a little persuasion wouldn’t hurt.
If reassurance arrives in the form of a VirusTotal report which declares that dozens of security companies tested the app and found nothing wrong, that’s merely a good start. The reality is that these companies are looking for certain types of behavior that piracy-focused apps tend not to display.
Since the topic offers the opportunity, today we’d like to mention a single piece of software that’s extremely easy to use, doesn’t cost a penny, and provides enough information to allow even a beginner to make an informed choice.
MobSF: Free and Easy to Use
Mobile Security Framework (or simply ‘MobSF’) is an all-in-one application that scans Android and iOS apps and provides a detailed security/malware analysis. If one has an APK file to hand, it’s simply a case of dragging the file into MobSF and waiting for the analysis to finish. That’s the first step and also the last, other than reading the generated report.
Installation instructions are available in MobSF’s GitHub repo for both Linux and Windows users, and for those without either, MobSF provides a live demo accessible via a web browser.
After scanning the app, a generated report begins with three or four pages of straightforward information, a few pieces of which we’ve quickly edited together in the image below. Item 3 actually appears first in the report and amounts to an overall score out of 100. A total of 37 means that the streaming app we tested has pretty big issues.
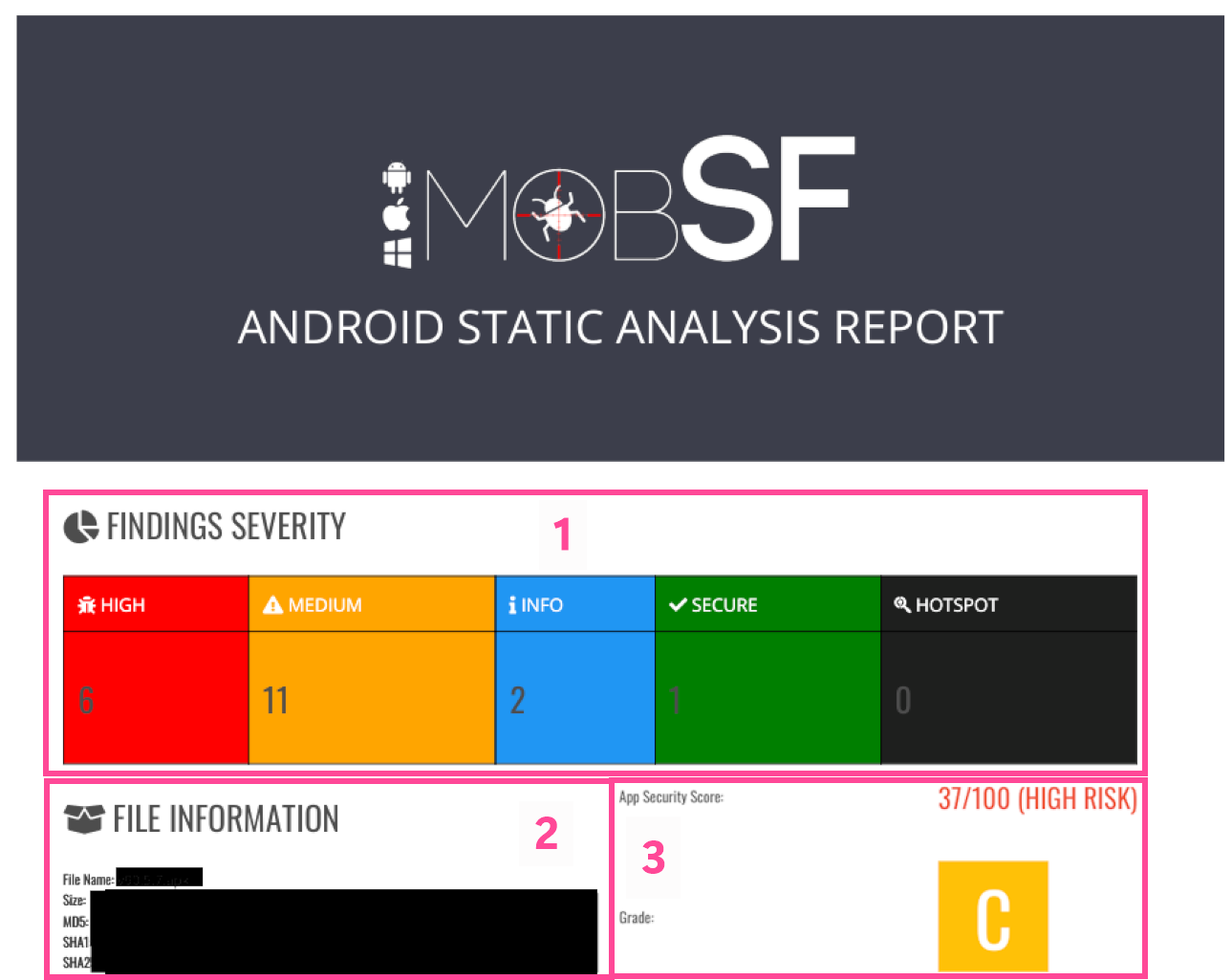
Item 2 provides basic information about the app including its name, filesize and hashes, while item 1 shows where the app had its most significant failings.
The reasons why the app failed are in the report and since even the most technical details receive a clear explanation, overall the report is pretty accessible, even if the exact terms aren’t immediately understood. More often that not, however, learning that an app can obtain the user’s GPS location, telephone number, contacts information, and for some reason has the ability to turn on the phone’s camera and microphone, is clear enough.
Even if very little is understood on the technical side, the report also supplies information about piracy apps unrelated to security, that most people never see but will definitely be intrigued to read.
For those already familiar with this type of report, MobSF also supports dynamic analysis with the assistance of an Android VM.
The discussion paper can be found here on the EUIPO website.
From: TF, for the latest news on copyright battles, piracy and more.
This post has been read 162 times!
